Table of Contents
a. Zscaler 101
Zscaler is a large player in network security. It competes with Palo Alto’s next-gen suite, Cloudflare and so many others. Zscaler’s Zero Trust Exchange (ZTE) is its overarching, cloud-native security platform. It blazes a trail between users, apps and devices across eligible networks. It’s increasingly involved in agentic and autonomous asset connections too.
Zero Trust is exactly what it sounds like: never trusting anything. The exchange vets and verifies all traffic as it moves within a company’s perimeter. It doesn’t allow bad actors to breach infrastructure weak spots and gain free access to everything else thereafter. That’s called “lateral threat movement.” It constantly verifies. Zscaler uses risk scores to assess security risk for every interaction, meaning it’s only creating user friction when there’s real security concern. This Zero Trust approach routinely cuts infrastructure costs for customers by shrinking the attack surface down, removing vulnerabilities and augmenting efficacy. ZTE replaces an antiquated firewall and virtual private network (VPN) setup in which fixed rules determine entry into the firewall-protected environment. Once that entry is granted, every device & user within a perimeter gets perpetual and unconditional access.
Product & Growth Pillar #1 – Zero Trust Everywhere
Zero Trust Everywhere (can’t call it ZTE because that’s the name of Zero Trust Exchange) is made up of its core network security products, branch-level security, and Zero Trust Cloud.
Core Network Security Products:
- Zscaler Internet Access (ZIA) protects internet connections. It’s the middleman between a user and a network that ensures proper authorization & access.
- Zscaler Private Access (ZPA) offers remote access to internal apps. It can directly connect to needed resources and destinations without public exposure (unlike VPNs).
- Zscaler Digital Experience (ZDX) optimizes cloud app performance and finds issues faster. It sifts through networks to identify sources holding back productivity to be fixed.
- Zscaler for Users is the firm’s bundle that combines ZIA, ZPA and ZDX.
Branch-Level Security:
For newer, ZPA-related products, Zero Trust Segmentation separates networks to offer more localized visibility. Branch security uses this capability to treat every single company location as its own island or network to shrink the attack surface. These “islands” (not entire enterprises) connect to single apps or network subsections only when needed. That’s called micro-segmentation. This lowers the risk of lateral threat movement by minimizing access. And it’s offered through a single appliance, meaning there’s one console for campuses, factories and retail shops. That reduces complexity and friction.
Zero Trust for branches upgrades legacy Software-Defined Wide Area Network (SD-Wan) functionality. As a reminder, SD-Wan is a digital manager of network connectivity. It splits network hardware and software-based control. This cuts costs, streamlines management & augments protection. SD-WAN is great for network optimization and can handle significant traffic routing needs. But? This requires direct appliance installation and does run into security concerns. Zscaler Branch Security doesn’t require hefty hardware installation. Just a cloud-native branch connector and a virtual machine (VM) to seamlessly turn on.
Zero Trust Cloud:
Zero Trust Cloud is Zscaler’s name for cloud app and workload use cases within its core network security products. It also offers configuration analysis and cloud workload protection products.
Product & Growth Pillar #2 – Data Security Everywhere:
Zscaler Data Fabric is the term it uses for openly integrating with a long list of needed data sources. It handles ingestion, organization, “harmonization” and the unleashing of this lucrative context. Zscaler offers data security across endpoints, email, web, GenAI apps and legacy software. That makes sense. If it’s already protecting so much of the world’s network traffic… and if it already leverages all of this data (structured and unstructured) … that gives it a head start on using this insight to offer more products.
- Data security posture management (DSPM) granularly tags, organizes and protects cloud-native data.
- Data Loss Prevention (DLP) guards clients against data leakage or theft for emails, endpoints, networks and more.
- It also offers encryption tools.
- Data Security Everywhere is the name of the unified suite.
Product & Growth Pillar #3 – “Agentic Operations:”
This category includes security operations (SecOps), IT Operations (ITOps) and all other AI product innovation.
ITOps includes products like its AI Copilot for ZDX (GenAI assistant) and ZDX Network Intelligence. This tracks internet service provider (ISP) performance. It readily uses outage data to refine Zscaler’s zero trust exchange efficacy, which helps performance and up-time.
Within SecOps:
- Unified Vulnerability Management (UVM) offers a bird's-eye view across 150+ data sources to tag, assess and remediate vulnerabilities across all identities as well as cloud and on-premise environments. It ranks all issues, prioritizes pressing items and offers the best course of action for remediation.
- Risk360 leverages UVM’s holistic view of vulnerabilities and enhances it with Zscaler and 3P signals. It then maps potential cyber risks and ranks them by potential financial damage. It also gives the best next steps of remediation.
- Business Insights: Broad visibility into app usage, costs, needs and engagement. This helps minimize unneeded apps and licenses.
- The aforementioned Data Fabric tool is also a big part of this product suite.
- This also includes its Managed Detection and Response (MDR) product acquired via Red Canary M&A. This blends AI-based and expert security analyst protection.
For AI, it has a well-established GenAI Security business in safeguarding companies from sensitive data leakage associated with 1st and 3rd-party AI apps. It’s also now directly protecting these AI assets (public and private) with AI Guard and is building on this presence with M&A and product expansion. More on that later.
b. Key Points
- AI security momentum is excellent.
- Platform-wide adoption is outperforming expectations.
- Small raises to annual guidance.
- Resilient margins despite a focus on product scaling over margin optimization.
c. Demand
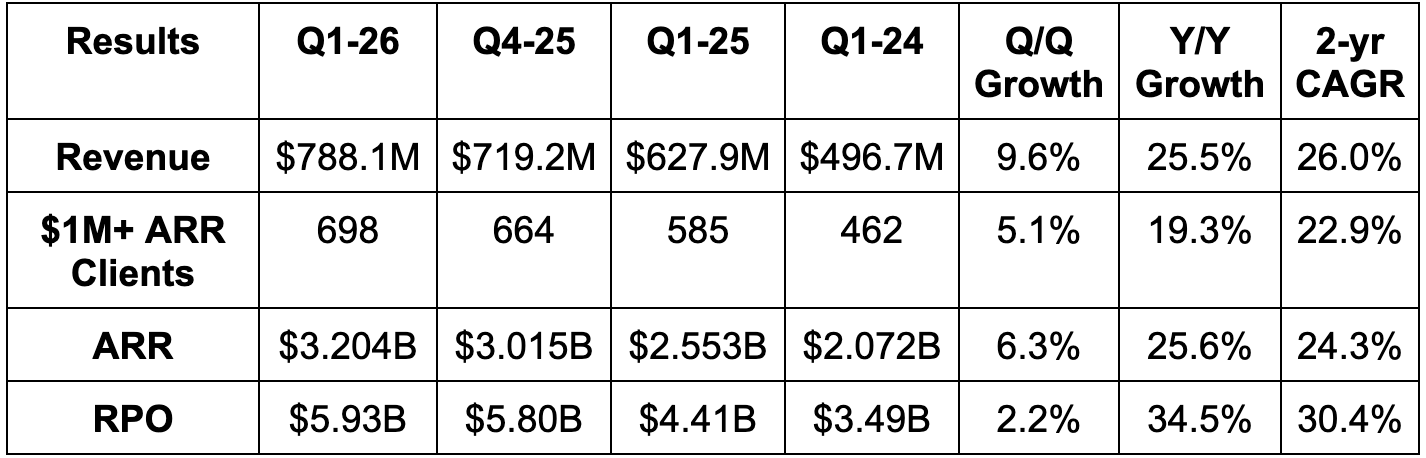
- Beat revenue estimates by 1.8% & beat guidance by 1.9%.
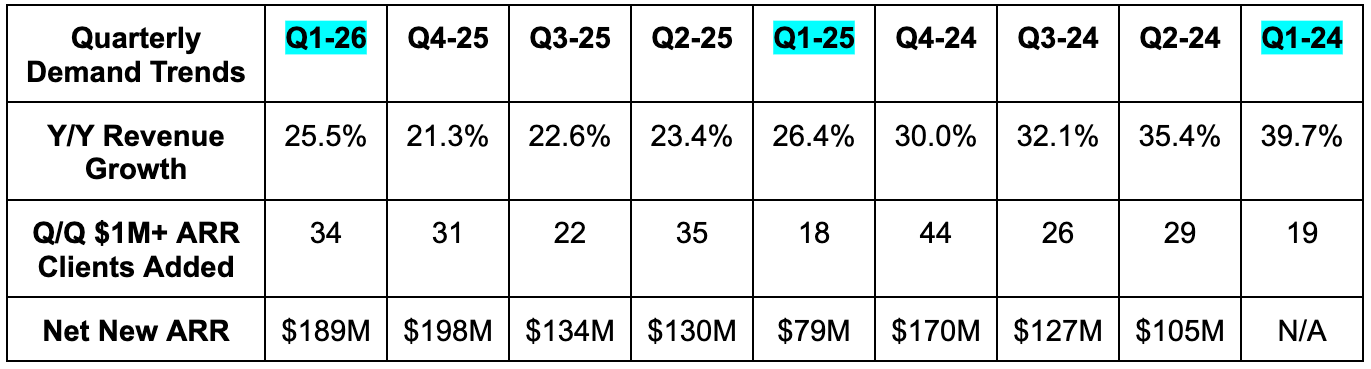
- 26.0% 2-year revenue compounded annual growth rate (CAGR) vs. 25.7% Q/Q 27.2% 2 quarters ago.
- Beat $167M net new ARR estimate by $22M.
- Organic ARR growth was stable Q/Q at around 22% Y/Y, with the acceleration driven by Red Canary M&A.
- Beat 694 $1M ARR client estimates by 4 customers.
- Beat remaining performance obligation (RPO) estimates by 5% or more. They rounded to $5.9B in the call when they disclosed the metric and called it 35% Y/Y growth. This compares to 31% Y/Y growth last quarter. The quarterly filing hasn’t been published yet, so that’s what we have. I was conservative and assumed 35% Y/Y growth meant 34.5% Y/Y. Actual RPO could be slightly higher than what you see in the chart below. When in doubt… round down. And regardless of rounding, 34.5% Y/Y RPO growth is a great sign of strong forward-looking demand. It got some help from longer duration, as current RPO is 47% of total vs. 49% Y/Y, but still very good.
As we’ll dig into during the guidance part of this review, Red Canary M&A had a small impact on outperformance. At the same time, organic ARR across all of its product categories exceeded expectations and accelerated. That was great to hear. Furthermore, organic ARR growth was roughly 22% Y/Y and stable compared to last quarter.
d. Profits
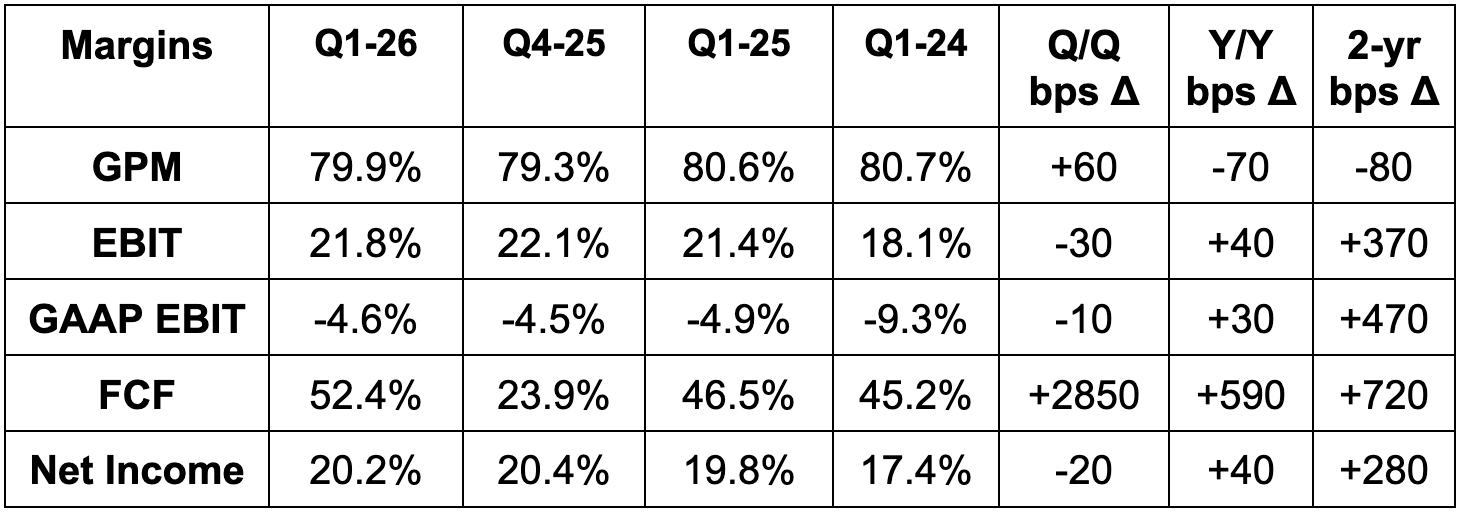
- Met GPM estimates & met guidance.
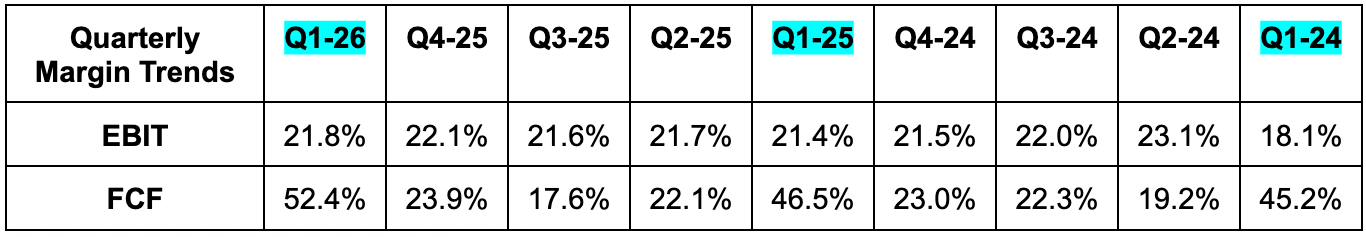
- They’re in new product introduction and scaling mode. They are not focused on GPM optimization. That will come later, yet they still are at a lofty 80% margin.
- Beat EBIT estimate by 2.3% & beat guidance by 2.9%.
- OpEx rose by 23% Y/Y.
- Beat $0.86 EPS estimate by $0.10 beat guidance by $0.105.
- The tax rate was 23% as expected.
- Beat FCF estimate by 17%.
- Quarterly FCF is highly influenced by timing of billings and CapEx.
e. Balance Sheet
- $3.5B cash & equivalents.
- $1.7B convertible notes.
- 3.2% Y/Y share dilution.
f. Guidance & Valuation
Q2 revenue & EPS guidance slightly ahead & slight miss for EBIT.
For the full year, Zscaler:
- Raised annual ARR guidance by 0.6% or $21M.
- Raised annual revenue guidance by 0.5%, beating estimates by 0.4%.
- Raised annual EBIT guidance by 0.5%, slightly beating estimates.
- Raised annual $3.66 EPS guidance by $0.14, beating estimates by $0.12.
- Reiterated 26.25% FCF margin guidance, meaning FCF dollar guidance rose in line with revenue.
Zscaler says it now expects $500M in AI ARR for the year vs. $400M previously. This was mainly thanks to Red Canary M&A contributing another $95M to that bucket, with some modest organic strength adding to the raise. You may be rightfully wondering how this was raised by $100M if overall ARR was only raised by $21M. Did the rest of the business guidance get cut? No. Importantly, Red Canary was already part of the annual guidance ZS provided last quarter, as it talked about including $95M in Red Canary ARR in that guidance. At the same time, Red Canary is modestly outperforming those $95M ARR contribution expectations, so that boosted the overall $21M raise by a few million.
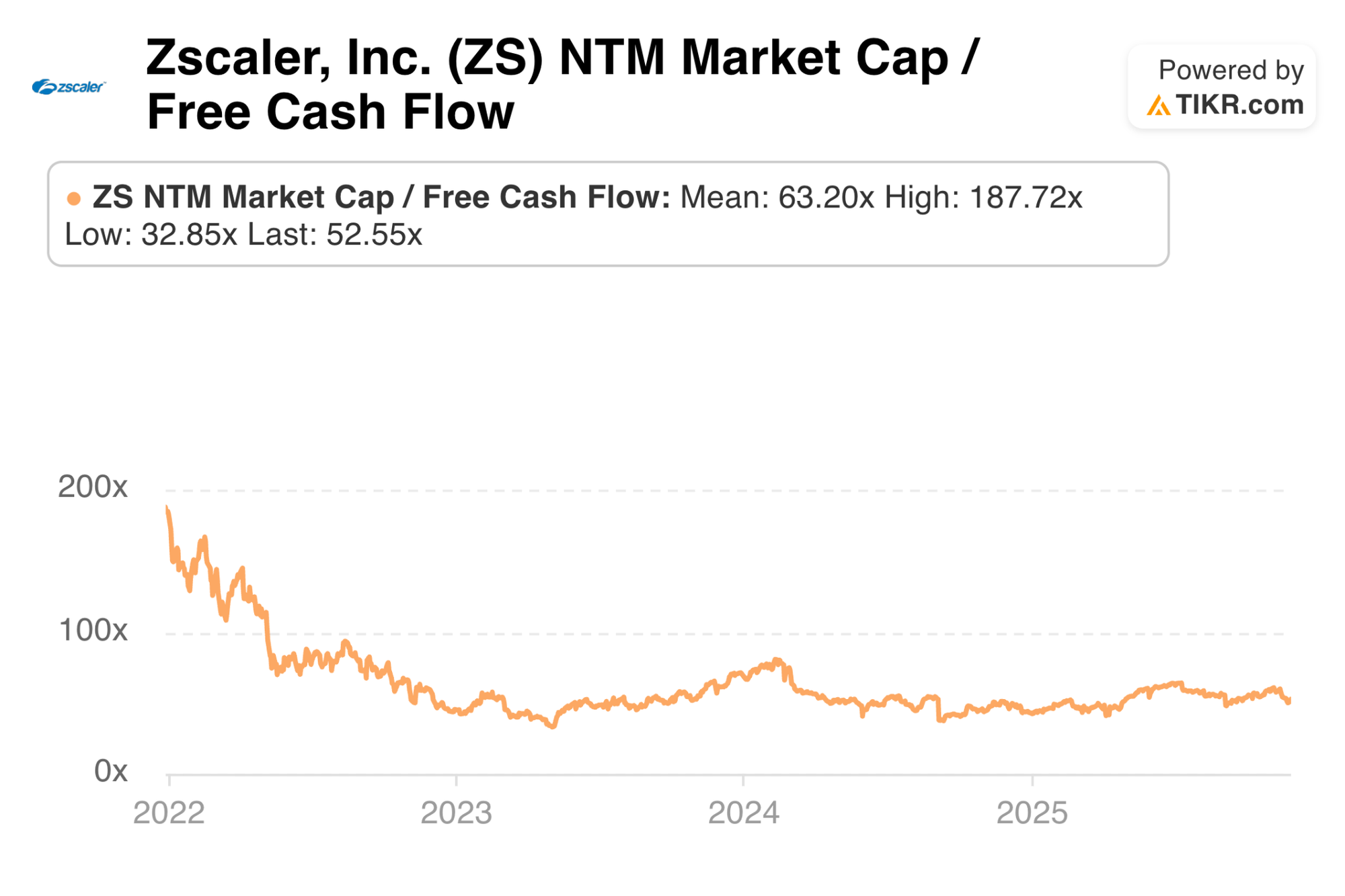
ZS likely trades for roughly 47x forward FCF following the beat and stock decline after-hours. FCF is expected to grow by 20% this year and then compound at a 3-year clip of nearly 27%.
g. Call & Release
Expanding the AI Offering – Security for AI Apps:
Zscaler is expanding AI focus to securing AI assets. It already had AI Security Posture Management (SPM) tools that protected customers against poor usage of AI apps leading to sensitive data leakage (GenAI Security). Now, with SPLX acquired, it gained a lot of assets to enrich its offering with AI asset inventory, governance and supply chain control. And with SPLX, the existing AI Guard tool can now effectively secure more AI models, agentic workflows and model context protocols (MCPs). Interestingly, SPLX also enables Zscaler to protect these assets closer to their actual development, rather than having to wait until deployment to stop breaches. That means finding issues before runtime and remediating before a headache. Beyond AI-SPM and related asset discovery tools, SPLX boasts AI Red Teaming capabilities (attack simulating) to test AI assets in a low-risk environment. This tightly integrates with customer software development pipelines to make usage quite seamless.
As I said a few weeks ago, SPLX was a solid M&A decision in my mind. It makes ZS a better AI security partner, as it pushes them more deeply into AI model and app security. They view this as great tech at a fair price that delivers solid total addressable market (TAM) expansion. It makes them more of a complete security platform in a world obsessed with point solution displacement.
- AI-SPM added a Global 2000 manufacturer and “leading” software and insurance companies this quarter.
- AI Guard added large consulting and healthcare companies this quarter.
Agentic AI Operations:
SecOps landed a Fortune 500 financial service company and two Global 2000s.
ZDX Advanced Plus bookings rose by 80% Y/Y. This is where its agentic ITOps products reside and is a strong sign of healthy traction.
ZDX introduced a few new innovations this quarter. First, it added end-to-end visibility of networks, applications and devices from one place, delivering a unified observability suite across a wide array of assets. This should expedite root cause analysis and mean time to resolution (MTTR). It also debuted multipath visualization to show all potential app data traffic routes, helping IT efficiency. Next, it added device scoring to uncover endpoint issues more quickly. ZDX is quickly becoming a consolidated location for all asset observability, giving it another way to consolidate point solutions beyond strictly cybersecurity use cases.
Zero Trust Everywhere and More on Platform-Level Adoption:
It now has 450+ Zero Trust Everywhere customers 3 quarters ahead of schedule, as it added another 100 sequentially. This is important, as getting customers to this status is a powerful source of better retention, lifetime value, Zscaler margins and outcomes. They do not think anyone “comes close” to matching the product breadth of this offering, supporting the already strong retention and competitive advantages. As leadership often says, competitors may have a decent Zero Trust product for specifically user connections, but ZS thinks it dwarfs the level of Zero Trust-protected assets of others. Simply put, this product category is a vital part of its differentiated platform-wide push.
Separately, the more aggressive push from SAP to get its customers to a cloud-based version of their platform (SAP RISE) is great for Zero Trust for Cloud. This will give Zscaler a large batch of customers to more seamlessly pursue, with its ability to eliminate antiquated hardware, point solutions, cost and headache leading to probable success. When Microsoft migrated to Microsoft 365, that was a large boost for ZS’s business, and this could potentially be as well.
Finally, they’re excited about early traction for Branch security. They’ve only worked through about 10% of the potential selling opportunities across existing customers and think the 10% that have converted provide massive revenue expansion potential.
- Zero Trust Cloud secured an 8-figure TCV deal with a Fortune 500 brand.
- Zero Trust Cloud Gateway continues to deliver sub 10 minute Zero Trust Cloud deployment time for AWS. This is done without deploying separate hardware, apps or firewalls, lowering costs even further.
- Branch security facilitated a 3X ARR up-sell with a Global 2000 manufacturing firm.
ZFlex:
As a reminder, ZFlex is its updated module selling format that allows customers to more “flexibly” consume commitments and mix-and-match modules within existing contracts. This can be done without a formal procurement process, so it continues to shrink sales cycles and drive faster product adoption as hoped for. This quarter, its ability to inspire module experimentation and up-selling drove $175M in total contract value (TCV) vs. $100M last quarter and $65M 2 quarters ago. It also facilitated multiple 9-module upsells to a couple large customers.
Data Security Everywhere:
Data security crossed $450M in ARR as it added roughly $25M for a 3rd straight quarter. It secured some large wins, including one with a large healthcare provider for 5 data modules. It beat out a “leading” cloud access security broker (CASB) vendor for this deal.
Competition:
There are no changes to the competitive backdrop, as things have improved, if anything. They’re very pleased with pipeline levels and win rates and think they’re distancing themselves from the pack.
More Notes:
- Crossed $1B in cumulative sales through the AWS marketplace.
- Debuted FedRamp Moderate authorized data centers in London and Paris to give U.S. agencies more flexible and compliant access to tools.
h. Take
There were likely some buy-side analysts looking for bigger beats and raises and perhaps some concern over how much of the ARR strength was M&A-fueled.
With that said, I think those negatives are very modest and overshadowed by a much longer list of positives. This was another solid quarter. Zscaler is showing everyone that it has plenty of runway to keep growing ARR at an organic 20% Y/Y clip. They are enjoying rock-solid traction across every single growth vector and greatly outpacing their own hopes for pace of platform-wide adoption. Its most mature products continue to find solid (accelerating) growth too. The margin trajectory remains great and the SPLX M&A is something I wholeheartedly support. It's greatly bolstering their presence in a budding AI security field that they need to be a big part of… which is what I fully expect. This is a world-class security platform that dominates in the network and is starting to dominate elsewhere too. They have so much cross-selling left to enjoy and still so much room for new customer growth.
At roughly 47x FCF and 26% multi-year FCF compounding, I think this great company is fairly-priced. I’d entertain adding to my stake at a growth multiple closer to 1.7x, which is right around $250/share. Who knows, maybe I'll get that chance tomorrow. Maybe not. All I know is that this company is doing everything I need it to do for me to stay a confident shareholder. I’m happy to continue owning what I own if this sell-off proves short-lived. We shall see.

